Just Some Avocado Writeup - scriptCTF 2025
My writeup for the "Just Some Avocado" forensics challenge in scriptCTF 2025
Just Some Avocado (302pts)
just an innocent little avocado!
Initial Thoughts
We are given an image file, avocado.jpg. Because it is a forensics challenge, the first thing to check is stegonography.
Methodology
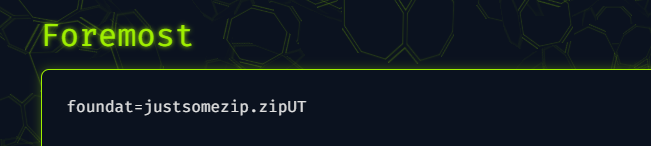
I uploaded the image into Aperi’solve, and foremost found a zip file.
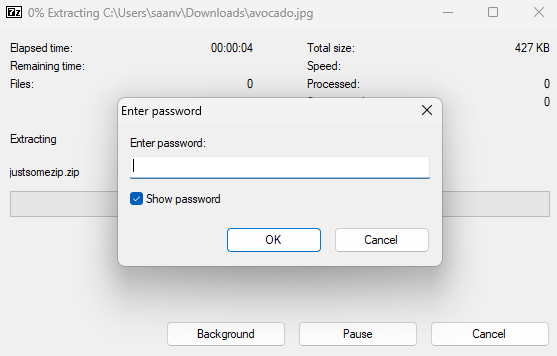
Unfortunately, the zip file requires a password.
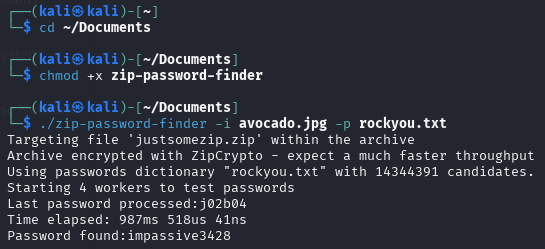
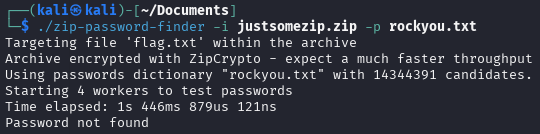
Using zip-password-finder and rockyou, we find the password impassive3428.
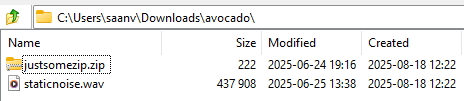
Unzipping the file shows staticnoise.wav and justsomezip.zip.
Unfortunately, justsomezip.zip is password protected. However, it does seem to contain the flag.
This means that staticnoise.wav must have the password hidden somehow. The audio is, just as it says, static noise. This means that it’s probably not morse code or garbled text in the audio file itself.
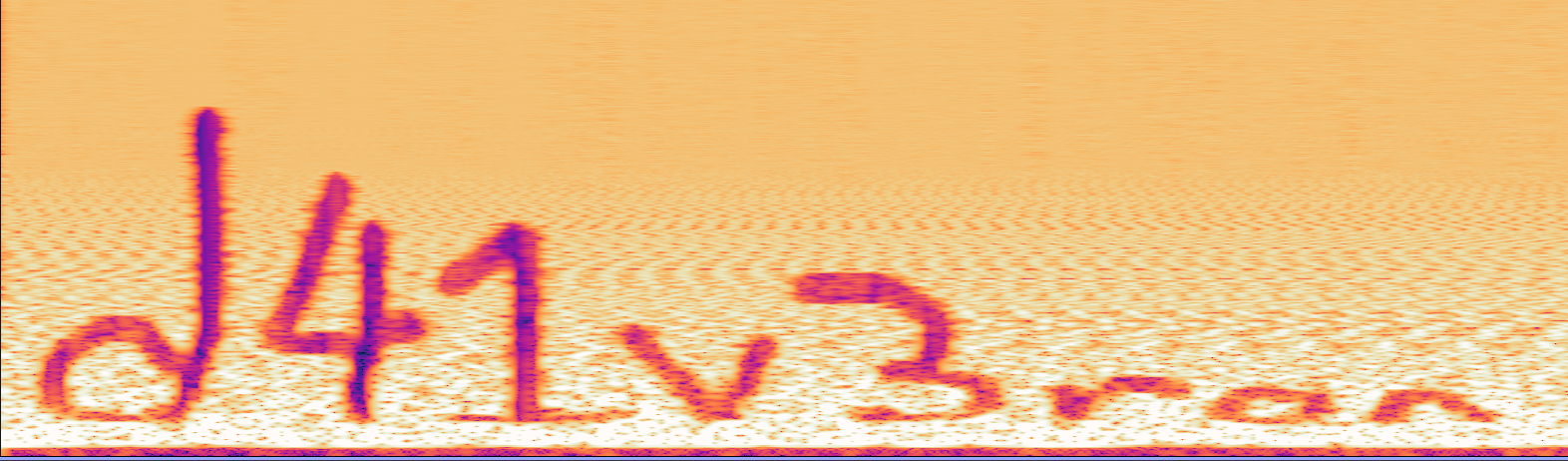
The next thing to check is spectograms. Sometimes audio files have hidden pictures/text “drawn” on the wavelengths that are revealed when you view the spectogram.
I upload staticnoise.wav into Audacity and switch it to spectogram view.
This reveals a hidden message of d41v3ron. Using that as the password for justsomezip.zip works.
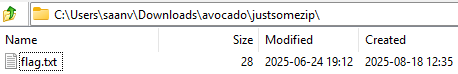
Finally, we find flag.txt.
Solution
The flag is scriptCTF{1_l0ve_d41_v3r0n}. This was a relatively simple forensics challenge that combined numerous basic techniques, and I had fun.